A Glimpse into ZTE Security’s Blueprint for Digital Safety
In our interconnected world, cyberattacks pose an ever-present danger. But not every organization faces equal risks. Providers of essential infrastructure carry heightened accountability to secure the very systems entire nations rely upon. Fulfilling this immense responsibility necessitates strategic rigor reflecting their specialized technology, regulations, and threat landscape.
As a leading global telecom equipment and network solutions provider, ZTE security is squarely in this crucial role. With over 500 operators across 160+ countries dependent on their infrastructure, cyber defense lies at the heart of ZTE’s mission. This led ZTE to formulate a forward-thinking security philosophy of prevention and transparency to safeguard their customers. This article explores the comprehensive strategies and initiatives underpinning ZTE Security’s digital safety approach.
ZTE’s Philosophy on Cybersecurity

ZTE recognizes that security serves as the foundation for everything they create. This led to developing their forward-thinking cybersecurity philosophy rooted in two core tenets – “Security in DNA” and “Trust through transparency”.
“Security in DNA” stresses intrinsically integrating defenses into the origins of infrastructure, not as an afterthought. Flaws embedded in the core cannot be fully resolved through subsequent layers. So ZTE focuses on preventively baking in security from the initial design stage.
Extensive testing like threat modeling and static/dynamic analysis spots issues pre-development. Customized chips and operating systems enable security by design controls. Rigorous protocols maintain security hygiene throughout manufacturing, supply chain and delivery processes.
By embedding security into the underlying DNA of infrastructure, ZTE aims to engineer products resilient against attacks targeting fundamental levels. This inside-out approach reflects their philosophy of prevention over-reactive response.
The “Trust through transparency” prong focuses on open collaboration to advance best practices. ZTE views cyber safety as a collective responsibility requiring cross-sector cooperation. As a member of over 100 international security bodies, ZTE engages with public and private sector experts worldwide to shape standards and solutions.
By contributing their knowledge and working transparently with partners, ZTE seeks to build greater trust and foster an ecosystem where all participants share the duty of securing our digital landscape.
ZTE’s cybersecurity philosophy drives its extensive efforts to integrate cutting-edge defenses into the core of essential infrastructure while working cooperatively across the industry to enable collective protection.
Risk-based Cybersecurity Practices
ZTE rejects a one-size-fits-all approach to security. They recognize threat exposure depends heavily on each organization’s unique technology environment, regulations, data sensitivities, and footprint. What represents mission-critical vulnerabilities for a utility can differ vastly from those of a financial institution.
So ZTE conducts in-depth assessments to spotlight the most pressing dangers and priorities based on the customer’s specific landscape – their business processes, data assets, infrastructure, applications, and use cases.
These insights inform prescriptive recommendations precisely calibrated to mitigate customer-specific risks. Steps may involve adopting new safeguards, hardening networks, sharpening monitoring/detection, improving incident response plans, and more.
Reviews are then conducted periodically to realign defenses as the threat landscape evolves. New regulations, technology expansions, and more can significantly alter risk exposure profiles. Continual fine-tuning of controls keeps security strategically on pace with shifts that may introduce new vulnerabilities.
This precision approach recognizes limited security budgets. With focused targeting, organizations get resilient protection concentrating resources around assessed top priority exposures rather than diluting efforts.
Cybersecurity Governance Architecture
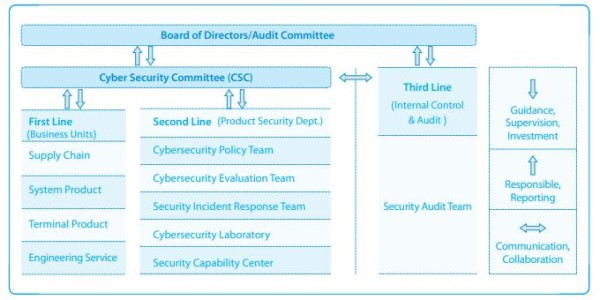
To enable robust security governance, ZTE employs a coordinated ‘three lines of defense’ model across its hierarchy.
The first line has internal departments integrate security practices into their operations per ZTE’s centralized policies and frameworks. Localized implementation intrinsically embeds security controls distributed across the organization.
The second line oversees policies, maintains standards, assesses risks, and guides first-line implementation. Centralized oversight fosters consistency, best practice compliance, and resource optimization.
Third-line audits and reviews validate control efficacy via internal and independent external assessments benchmarked against industry standards. Gaps identified enable continuous improvement.
This blended model combines localized agility to address distinct needs with centralized visibility. First-line implementation reflects each environment’s priorities, while second and third lines enable comprehensive oversight.
ZTE’s three-line model provides the frameworks, compliance, and visibility for security orchestration company-wide. It also allows tailored application within business units that fits their unique risks.
By synergizing decentralized and centralized governance, ZTE achieves multilayered cybersecurity capable of securing expansive digital infrastructure across a complex, evolving threat landscape.
This multifaceted approach enables ZTE to implement progressive security strategies vital for protecting the critical systems entire nations rely upon in today’s interconnected world.
Full Product Life Cycle Assurance
Recognizing that security requires vigilance across the entire product lifespan, ZTE implements multilayered protections spanning the full life cycle.
In the design phase, ZTE utilizes threat modeling, architecture analysis, and other processes to identify and minimize risks upfront before development even begins. Creating its own custom chips, boards, operating systems and more enhances control over “security by design”.
Specialized analysis like fuzz testing further strengthens hardware and software security in production. Strict version control, access restrictions and more boost defenses across the integrated manufacturing and supply chains.
Comprehensive protocols also secure warehousing, logistics and delivery against tampering, counterfeits and other supply chain threats. Procurement and supplier reviews additionally minimize vulnerabilities entering via third-parties.
Post-deployment, ZTE provides continuous security maintenance, including monitoring, updates and proactive improvements. The company issues security advisories and patches promptly upon identifying vulnerabilities. Incident response mechanisms allow rapid investigation and remediation in case of any breach.
For services and cloud offerings, ZTE conducts in-depth customer data security assessments factoring legal obligations, data criticality and client environments. Multi-level data governance and controls provide sustained data protection.
By weaving security protections into each phase from idea to end-of-life, ZTE delivers trustworthy products and solutions ready for the rigors of operational environments. This uncompromising life cycle view cements ZTE’s commitment to being a guardian of digital safety.
Conclusion
With “Security in DNA, trust through transparency” as its guiding light, ZTE integrates proactive threat protection, dynamic risk management, stringent governance and full life cycle security to ensure comprehensive digital safety. The multilayered ZTE security blueprint helps strengthen cybersecurity ecosystems and fosters greater trust in the digital future. As technologies continue to advance, ZTE remains committed to upholding the highest standards of security to enable sustainable digital transformation.
Media Contact
Company Name: ZTE Corporation
Contact Person: Lunitta LU
Email: Send Email
Country: China
Website: https://www.zte.com.cn/global/